Control Channel SSL/Data dynamic negotiation Module This file is split from ssl.h to be able to unit test it. More...
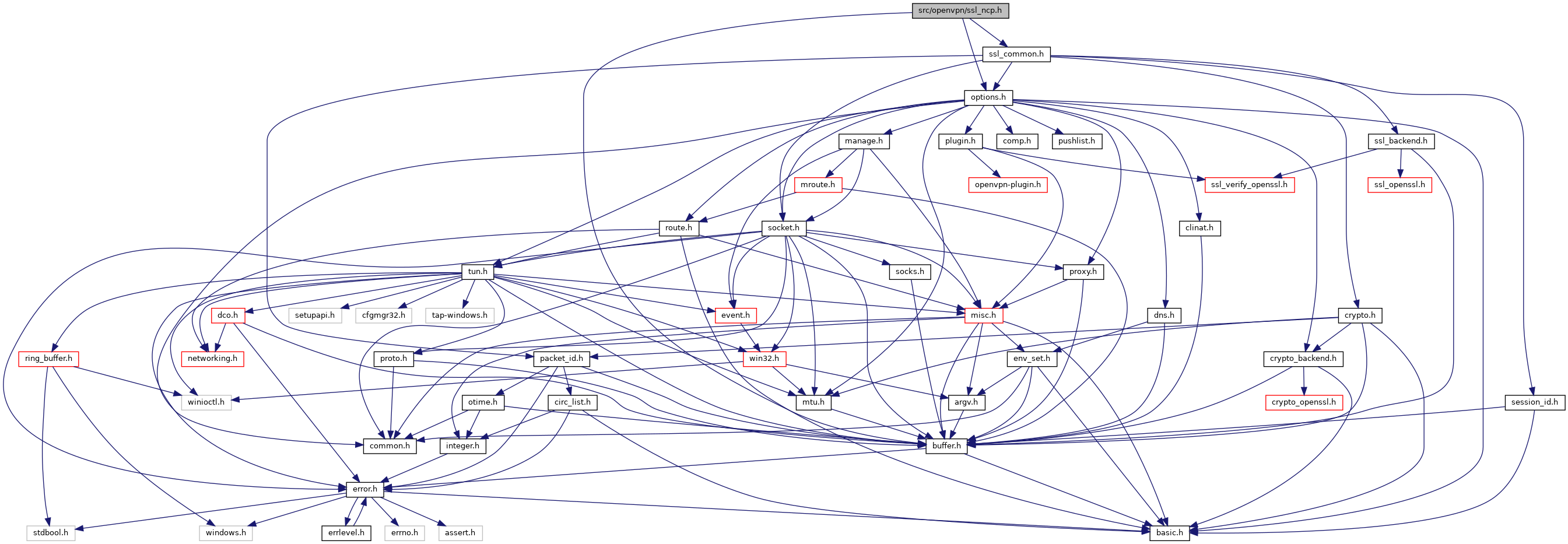
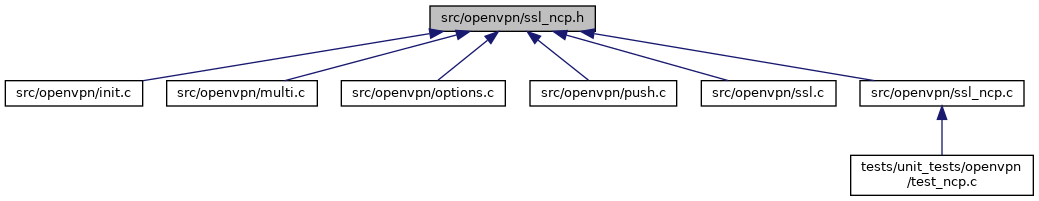
Go to the source code of this file.
Macros | |
| #define | MAX_NCP_CIPHERS_LENGTH 127 |
| The maximum length of a ncp-cipher string that is accepted. | |
Functions | |
| bool | tls_peer_supports_ncp (const char *peer_info) |
| Returns whether the client supports NCP either by announcing IV_NCP>=2 or the IV_CIPHERS list. | |
| bool | check_pull_client_ncp (struct context *c, unsigned int found) |
| Checks whether the cipher negotiation is in an acceptable state and we continue to connect or should abort. | |
| char * | ncp_get_best_cipher (const char *server_list, const char *peer_info, const char *remote_cipher, struct gc_arena *gc) |
| Iterates through the ciphers in server_list and return the first cipher that is also supported by the peer according to the IV_NCP and IV_CIPHER values in peer_info. | |
| const char * | tls_peer_ncp_list (const char *peer_info, struct gc_arena *gc) |
| Returns the support cipher list from the peer according to the IV_NCP and IV_CIPHER values in peer_info. | |
| char * | mutate_ncp_cipher_list (const char *list, struct gc_arena *gc) |
| Check whether the ciphers in the supplied list are supported. | |
| void | append_cipher_to_ncp_list (struct options *o, const char *ciphername) |
| Appends the cipher specified by the ciphernamer parameter to to the o->ncp_ciphers list. | |
| bool | tls_item_in_cipher_list (const char *item, const char *list) |
| Return true iff item is present in the colon-separated zero-terminated cipher list. | |
| void | p2p_mode_ncp (struct tls_multi *multi, struct tls_session *session) |
| Determines if there is common cipher of both peer by looking at the IV_CIPHER peer info. | |
| const char * | get_p2p_ncp_cipher (struct tls_session *session, const char *peer_info, struct gc_arena *gc) |
| Determines the best common cipher from both peers IV_CIPHER lists. | |
| bool | check_session_cipher (struct tls_session *session, struct options *options) |
| Checks if the cipher is allowed, otherwise returns false and reset the cipher to the config cipher. | |
| void | options_postprocess_setdefault_ncpciphers (struct options *o) |
| Checks for availability of Chacha20-Poly1305 and sets the ncp_cipher to either AES-256-GCM:AES-128-GCM or AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 if not set. | |
| const char * | ncp_expanded_ciphers (struct options *o, struct gc_arena *gc) |
| returns the o->ncp_ciphers in brackets, e.g. | |
Detailed Description
Control Channel SSL/Data dynamic negotiation Module This file is split from ssl.h to be able to unit test it.
Definition in file ssl_ncp.h.
Macro Definition Documentation
◆ MAX_NCP_CIPHERS_LENGTH
| #define MAX_NCP_CIPHERS_LENGTH 127 |
Function Documentation
◆ append_cipher_to_ncp_list()
| void append_cipher_to_ncp_list | ( | struct options * | o, |
| const char * | ciphername | ||
| ) |
Appends the cipher specified by the ciphernamer parameter to to the o->ncp_ciphers list.
- Parameters
-
o options struct to modify. Its gc is also used ciphername the ciphername to add
Definition at line 195 of file ssl_ncp.c.
References ASSERT, gc_malloc(), and buffer::len.
Referenced by options_set_backwards_compatible_options().
◆ check_pull_client_ncp()
| bool check_pull_client_ncp | ( | struct context * | c, |
| unsigned int | found | ||
| ) |
Checks whether the cipher negotiation is in an acceptable state and we continue to connect or should abort.
- Returns
- Wether the client NCP process suceeded or failed
Definition at line 310 of file ssl_ncp.c.
References context::c2, D_PUSH_DEBUG, D_TLS_ERRORS, options::enable_ncp_fallback, msg, options::ncp_ciphers_conf, OPT_P_NCP, context::options, tls_multi::remote_ciphername, context_2::tls_multi, and tls_poor_mans_ncp().
Referenced by do_deferred_options().
◆ check_session_cipher()
| bool check_session_cipher | ( | struct tls_session * | session, |
| struct options * | options | ||
| ) |
Checks if the cipher is allowed, otherwise returns false and reset the cipher to the config cipher.
Definition at line 515 of file ssl_ncp.c.
References options::ciphername, D_TLS_ERRORS, options::enable_ncp_fallback, gc, gc_free(), gc_new(), buffer::len, msg, options::ncp_ciphers, options::ncp_ciphers_conf, ncp_expanded_ciphers(), streq, and tls_item_in_cipher_list().
Referenced by tls_session_update_crypto_params().
◆ get_p2p_ncp_cipher()
| const char * get_p2p_ncp_cipher | ( | struct tls_session * | session, |
| const char * | peer_info, | ||
| struct gc_arena * | gc | ||
| ) |
Determines the best common cipher from both peers IV_CIPHER lists.
The first cipher from the tls-server that is also in the tls-client IV_CIPHER list will be returned. If no common cipher can be found, both peer will continue to use whatever cipher is their default and NULL will be returned.
- Parameters
-
session tls_session peer_info peer info of the peer gc gc arena that will be used to allocate the returned cipher
- Returns
- common cipher if one exist.
Definition at line 355 of file ssl_ncp.c.
References extract_var_peer_info(), gc, gc_free(), gc_new(), string_alloc(), strsep(), and tls_item_in_cipher_list().
Referenced by do_deferred_p2p_ncp(), and p2p_mode_ncp().
◆ mutate_ncp_cipher_list()
| char * mutate_ncp_cipher_list | ( | const char * | list, |
| struct gc_arena * | gc | ||
| ) |
Check whether the ciphers in the supplied list are supported.
- Parameters
-
list Colon-separated list of ciphers gc gc_arena to allocate the returned string
- Returns
- colon separated string of normalised (via translate_cipher_name_from_openvpn) and zero terminated string iff all ciphers in list are supported and the total length is short than MAX_NCP_CIPHERS_LENGTH. NULL otherwise.
Definition at line 96 of file ssl_ncp.c.
References alloc_buf(), buf_forward_capacity(), buf_len(), buf_null_terminate(), buf_puts(), buf_str(), cipher_kt_mode_aead(), cipher_kt_mode_cbc(), cipher_kt_mode_ofb_cfb(), cipher_kt_name(), cipher_valid(), free_buf(), gc, buffer::len, M_WARN, MAX_NCP_CIPHERS_LENGTH, msg, and string_alloc().
Referenced by options_postprocess_mutate(), and test_check_ncp_ciphers_list().
◆ ncp_expanded_ciphers()
returns the o->ncp_ciphers in brackets, e.g.
(AES-256-GCM:CHACHA20-POLY1305) if o->ncp_ciphers_conf and o->ncp_ciphers differ, otherwise an empty string
The returned string will be allocated in the passed gc
Definition at line 619 of file ssl_ncp.c.
References alloc_buf_gc(), BSTR, buf_printf(), gc, and buffer::len.
Referenced by check_session_cipher(), multi_client_set_protocol_options(), and test_ncp_expand().
◆ ncp_get_best_cipher()
| char * ncp_get_best_cipher | ( | const char * | server_list, |
| const char * | peer_info, | ||
| const char * | remote_cipher, | ||
| struct gc_arena * | gc | ||
| ) |
Iterates through the ciphers in server_list and return the first cipher that is also supported by the peer according to the IV_NCP and IV_CIPHER values in peer_info.
We also accept a cipher that is the remote cipher of the client for "Poor man's NCP": Use peer cipher if it is an allowed (NCP) cipher. Allows non-NCP peers to upgrade their cipher individually.
Make sure to call tls_session_update_crypto_params() after calling this function.
- Parameters
-
server_list Our own cipher list peer_info Peer information remote_cipher Fallback cipher, ignored if peer sent IV_CIPHERSgc gc arena that is used to allocate the returned string
- Returns
- NULL if no common cipher is available, otherwise the best common cipher
Definition at line 246 of file ssl_ncp.c.
References gc, gc_free(), gc_new(), streq, string_alloc(), strsep(), tls_item_in_cipher_list(), and tls_peer_ncp_list().
Referenced by multi_client_set_protocol_options(), test_ncp_best(), and test_poor_man().
◆ options_postprocess_setdefault_ncpciphers()
| void options_postprocess_setdefault_ncpciphers | ( | struct options * | o | ) |
Checks for availability of Chacha20-Poly1305 and sets the ncp_cipher to either AES-256-GCM:AES-128-GCM or AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 if not set.
If DEFAULT is in the ncp_cipher string, it will be replaced by the default cipher string as defined above.
Checks for availability of Chacha20-Poly1305 and sets the ncp_cipher to either AES-256-GCM:AES-128-GCM or AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 if not set.
Definition at line 576 of file ssl_ncp.c.
References cipher_valid(), dco_enabled(), dco_get_supported_ciphers(), buffer::len, replace_default_in_ncp_ciphers_option(), and tls_item_in_cipher_list().
Referenced by options_postprocess_mutate(), test_ncp_default(), and test_ncp_expand().
◆ p2p_mode_ncp()
| void p2p_mode_ncp | ( | struct tls_multi * | multi, |
| struct tls_session * | session | ||
| ) |
Determines if there is common cipher of both peer by looking at the IV_CIPHER peer info.
In contrast of the server mode NCP that tries to accomandate all kind of corner cases in P2P mode NCP only takes IV_CIPHER into account and falls back to previous behaviour if this fails.
Definition at line 472 of file ssl_ncp.c.
References alloc_buf_gc(), BSTR, buf_printf(), cipher_defined(), cipher_kt_name(), CO_EPOCH_DATA_KEY_FORMAT, CO_USE_TLS_KEY_MATERIAL_EXPORT, D_TLS_DEBUG_LOW, gc, gc_free(), gc_new(), get_p2p_ncp_cipher(), buffer::len, msg, p2p_ncp_set_options(), tls_multi::peer_id, tls_multi::peer_info, and tls_multi::use_peer_id.
Referenced by key_method_2_read(), and key_method_2_write().
◆ tls_item_in_cipher_list()
| bool tls_item_in_cipher_list | ( | const char * | item, |
| const char * | list | ||
| ) |
Return true iff item is present in the colon-separated zero-terminated cipher list.
Definition at line 206 of file ssl_ncp.c.
References buffer::len, and string_alloc().
Referenced by check_session_cipher(), do_init_crypto_tls_c1(), get_p2p_ncp_cipher(), ncp_get_best_cipher(), options_postprocess_cipher(), options_postprocess_setdefault_ncpciphers(), options_set_backwards_compatible_options(), options_string(), push_peer_info(), and tls_poor_mans_ncp().
◆ tls_peer_ncp_list()
| const char * tls_peer_ncp_list | ( | const char * | peer_info, |
| struct gc_arena * | gc | ||
| ) |
Returns the support cipher list from the peer according to the IV_NCP and IV_CIPHER values in peer_info.
- Returns
- Either a string containing the ncp list that is either static or allocated via gc. If no information is available an empty string ("") is returned.
Definition at line 225 of file ssl_ncp.c.
References extract_var_peer_info(), gc, buffer::len, and tls_peer_info_ncp_ver().
Referenced by multi_client_set_protocol_options(), ncp_get_best_cipher(), and test_extract_client_ciphers().
◆ tls_peer_supports_ncp()
| bool tls_peer_supports_ncp | ( | const char * | peer_info | ) |
Returns whether the client supports NCP either by announcing IV_NCP>=2 or the IV_CIPHERS list.
Definition at line 79 of file ssl_ncp.c.
References tls_peer_info_ncp_ver().
Referenced by prepare_push_reply(), and test_extract_client_ciphers().