Control Channel Common Data Structures. More...
#include "session_id.h"#include "socket_util.h"#include "packet_id.h"#include "crypto.h"#include "options.h"#include "ssl_backend.h"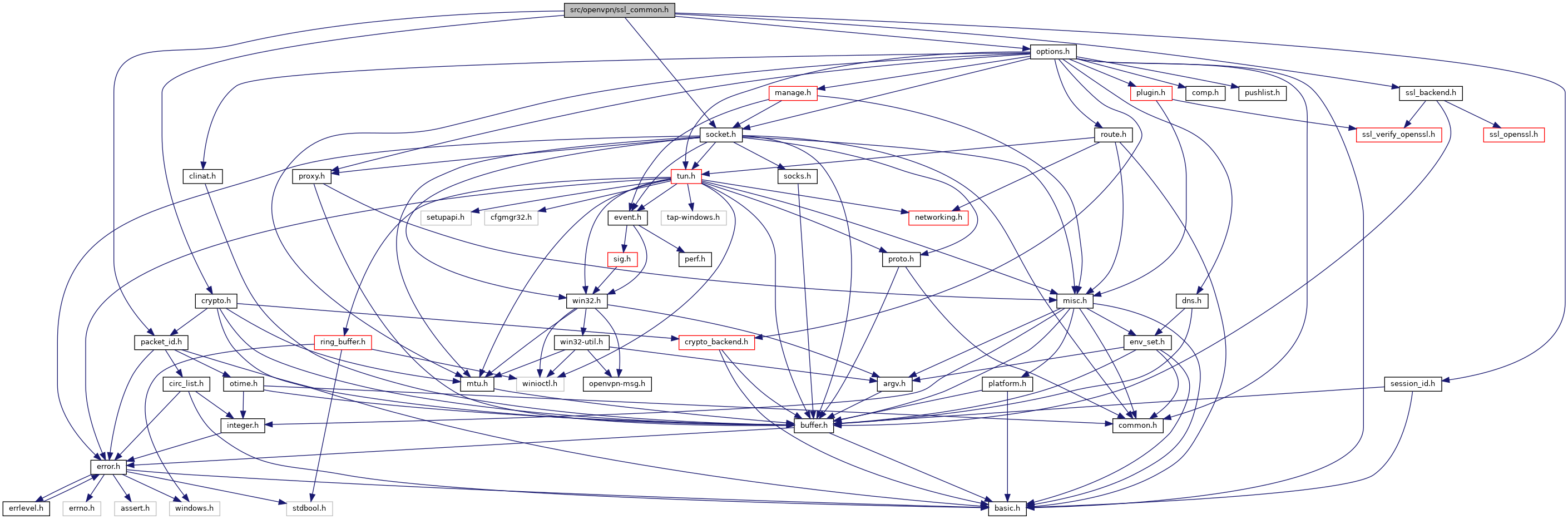
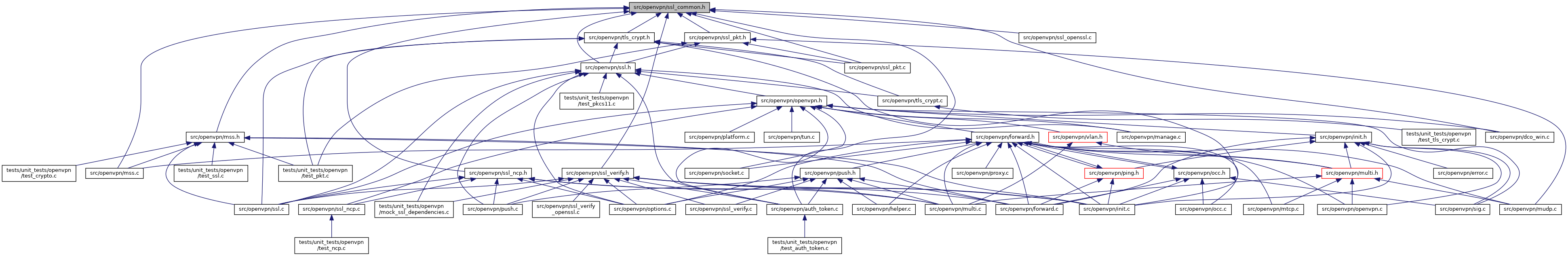
Go to the source code of this file.
Data Structures | |
| struct | key_source |
| Container for one half of random material to be used in key method 2 data channel key generation. More... | |
| struct | key_source2 |
| Container for both halves of random material to be used in key method 2 data channel key generation. More... | |
| struct | auth_deferred_status |
| struct | key_state |
| Security parameter state of one TLS and data channel key session. More... | |
| struct | tls_wrap_ctx |
| Control channel wrapping (–tls-auth/–tls-crypt) context. More... | |
| struct | tls_options |
| struct | tls_session |
| Security parameter state of a single session within a VPN tunnel. More... | |
| struct | tls_multi |
| Security parameter state for a single VPN tunnel. More... | |
Macros | |
| #define | UP_TYPE_AUTH "Auth" |
| #define | UP_TYPE_PRIVATE_KEY "Private Key" |
| #define | SSLF_CLIENT_CERT_NOT_REQUIRED (1u << 0) |
| #define | SSLF_CLIENT_CERT_OPTIONAL (1u << 1) |
| #define | SSLF_USERNAME_AS_COMMON_NAME (1u << 2) |
| #define | SSLF_AUTH_USER_PASS_OPTIONAL (1u << 3) |
| #define | SSLF_CRL_VERIFY_DIR (1u << 5) |
| #define | SSLF_TLS_VERSION_MIN_SHIFT 6 |
| #define | SSLF_TLS_VERSION_MIN_MASK 0xFu /* (uses bit positions 6 to 9) */ |
| #define | SSLF_TLS_VERSION_MAX_SHIFT 10 |
| #define | SSLF_TLS_VERSION_MAX_MASK 0xFu /* (uses bit positions 10 to 13) */ |
| #define | SSLF_TLS_DEBUG_ENABLED (1u << 14) |
| #define | KEY_SCAN_SIZE 3 |
| #define | AUTH_TOKEN_HMAC_OK (1 << 0) |
| Auth-token sent from client has valid hmac. | |
| #define | AUTH_TOKEN_EXPIRED (1 << 1) |
| Auth-token sent from client has expired. | |
| #define | AUTH_TOKEN_VALID_EMPTYUSER (1 << 2) |
| Auth-token is only valid for an empty username and not the username actually supplied from the client. | |
Control channel negotiation states | |
These states represent the different phases of control channel negotiation between OpenVPN peers. OpenVPN servers and clients progress through the states in a different order, because of their different roles during exchange of random material. The references to the Clients follow this order:
Servers follow the same order, except for | |
| #define | S_ERROR (-2) |
| Error state. | |
| #define | S_ERROR_PRE (-1) |
| Error state but try to send out alerts before killing the keystore and moving it to S_ERROR. | |
| #define | S_UNDEF 0 |
Undefined state, used after a key_state is cleaned up. | |
| #define | S_INITIAL 1 |
Initial key_state state after initialization by key_state_init() before start of three-way handshake. | |
| #define | S_PRE_START_SKIP 2 |
| Waiting for the remote OpenVPN peer to acknowledge during the initial three-way handshake. | |
| #define | S_PRE_START 3 |
| Waiting for the remote OpenVPN peer to acknowledge during the initial three-way handshake. | |
| #define | S_START 4 |
| Three-way handshake is complete, start of key exchange. | |
| #define | S_SENT_KEY 5 |
| Local OpenVPN process has sent its part of the key material. | |
| #define | S_GOT_KEY 6 |
| Local OpenVPN process has received the remote's part of the key material. | |
| #define | S_ACTIVE 7 |
Operational key_state state immediately after negotiation has completed while still within the handshake window. | |
| #define | S_GENERATED_KEYS 8 |
| The data channel keys have been generated The TLS session is fully authenticated when reaching this state. | |
Index of key_state objects within a tls_session structure | |
This is the index of | |
| #define | KS_PRIMARY 0 |
| Primary key state index. | |
| #define | KS_LAME_DUCK 1 |
| Key state index that will retire \ soon. | |
| #define | KS_SIZE 2 |
Size of the tls_session.key array. | |
Index of tls_session objects within a tls_multi structure | |
This is the index of Normally three tls_session objects are maintained by an active openvpn session. The first is the current, TLS authenticated session, the second is used to process connection requests from a new client that would usurp the current session if successfully authenticated, and the third is used as a repository for a "lame-duck" key in the event that the primary session resets due to error while the lame-duck key still has time left before its expiration. Lame duck keys are used to maintain the continuity of the data channel connection while a new key is being negotiated. | |
| #define | TM_ACTIVE 0 |
Active tls_session. | |
| #define | TM_INITIAL 1 |
As yet un-trusted tls_session \ being negotiated. | |
| #define | TM_LAME_DUCK 2 |
Old tls_session. | |
| #define | TM_SIZE 3 |
Size of the tls_multi.session \ array. | |
Enumerations | |
| enum | ks_auth_state { KS_AUTH_FALSE , KS_AUTH_DEFERRED , KS_AUTH_TRUE } |
| This reflects the (server side) authentication state after the TLS session has been established and key_method_2_read is called. More... | |
| enum | auth_deferred_result { ACF_PENDING , ACF_SUCCEEDED , ACF_DISABLED , ACF_FAILED } |
| enum | dco_key_status { DCO_NOT_INSTALLED , DCO_INSTALLED_PRIMARY , DCO_INSTALLED_SECONDARY } |
| enum | multi_status { CAS_NOT_CONNECTED , CAS_WAITING_AUTH , CAS_PENDING , CAS_PENDING_DEFERRED , CAS_PENDING_DEFERRED_PARTIAL , CAS_FAILED , CAS_WAITING_OPTIONS_IMPORT , CAS_RECONNECT_PENDING , CAS_CONNECT_DONE } |
Functions | |
| static struct key_state * | get_key_scan (struct tls_multi *multi, int index) |
gets an item of key_state objects in the order they should be scanned by data channel modules. | |
| static const struct key_state * | get_primary_key (const struct tls_multi *multi) |
gets an item of key_state objects in the order they should be scanned by data channel modules. | |
Detailed Description
Control Channel Common Data Structures.
Definition in file ssl_common.h.
Macro Definition Documentation
◆ AUTH_TOKEN_EXPIRED
| #define AUTH_TOKEN_EXPIRED (1 << 1) |
Auth-token sent from client has expired.
Definition at line 688 of file ssl_common.h.
◆ AUTH_TOKEN_HMAC_OK
| #define AUTH_TOKEN_HMAC_OK (1 << 0) |
Auth-token sent from client has valid hmac.
Definition at line 686 of file ssl_common.h.
◆ AUTH_TOKEN_VALID_EMPTYUSER
| #define AUTH_TOKEN_VALID_EMPTYUSER (1 << 2) |
Auth-token is only valid for an empty username and not the username actually supplied from the client.
OpenVPN 3 clients sometimes wipes or replaces the username with a username hint from their config.
Definition at line 696 of file ssl_common.h.
◆ KEY_SCAN_SIZE
| #define KEY_SCAN_SIZE 3 |
Definition at line 566 of file ssl_common.h.
◆ SSLF_AUTH_USER_PASS_OPTIONAL
| #define SSLF_AUTH_USER_PASS_OPTIONAL (1u << 3) |
Definition at line 426 of file ssl_common.h.
◆ SSLF_CLIENT_CERT_NOT_REQUIRED
| #define SSLF_CLIENT_CERT_NOT_REQUIRED (1u << 0) |
Definition at line 423 of file ssl_common.h.
◆ SSLF_CLIENT_CERT_OPTIONAL
| #define SSLF_CLIENT_CERT_OPTIONAL (1u << 1) |
Definition at line 424 of file ssl_common.h.
◆ SSLF_CRL_VERIFY_DIR
| #define SSLF_CRL_VERIFY_DIR (1u << 5) |
Definition at line 428 of file ssl_common.h.
◆ SSLF_TLS_DEBUG_ENABLED
| #define SSLF_TLS_DEBUG_ENABLED (1u << 14) |
Definition at line 433 of file ssl_common.h.
◆ SSLF_TLS_VERSION_MAX_MASK
| #define SSLF_TLS_VERSION_MAX_MASK 0xFu /* (uses bit positions 10 to 13) */ |
Definition at line 432 of file ssl_common.h.
◆ SSLF_TLS_VERSION_MAX_SHIFT
| #define SSLF_TLS_VERSION_MAX_SHIFT 10 |
Definition at line 431 of file ssl_common.h.
◆ SSLF_TLS_VERSION_MIN_MASK
| #define SSLF_TLS_VERSION_MIN_MASK 0xFu /* (uses bit positions 6 to 9) */ |
Definition at line 430 of file ssl_common.h.
◆ SSLF_TLS_VERSION_MIN_SHIFT
| #define SSLF_TLS_VERSION_MIN_SHIFT 6 |
Definition at line 429 of file ssl_common.h.
◆ SSLF_USERNAME_AS_COMMON_NAME
| #define SSLF_USERNAME_AS_COMMON_NAME (1u << 2) |
Definition at line 425 of file ssl_common.h.
◆ UP_TYPE_AUTH
| #define UP_TYPE_AUTH "Auth" |
Definition at line 41 of file ssl_common.h.
◆ UP_TYPE_PRIVATE_KEY
| #define UP_TYPE_PRIVATE_KEY "Private Key" |
Definition at line 42 of file ssl_common.h.
Enumeration Type Documentation
◆ auth_deferred_result
| enum auth_deferred_result |
| Enumerator | |
|---|---|
| ACF_PENDING | deferred auth still pending |
| ACF_SUCCEEDED | deferred auth has suceeded |
| ACF_DISABLED | deferred auth is not used |
| ACF_FAILED | deferred auth has failed |
Definition at line 174 of file ssl_common.h.
◆ dco_key_status
| enum dco_key_status |
| Enumerator | |
|---|---|
| DCO_NOT_INSTALLED | |
| DCO_INSTALLED_PRIMARY | |
| DCO_INSTALLED_SECONDARY | |
Definition at line 182 of file ssl_common.h.
◆ ks_auth_state
| enum ks_auth_state |
This reflects the (server side) authentication state after the TLS session has been established and key_method_2_read is called.
If async auth is enabled the state will first move to KS_AUTH_DEFERRED before eventually being set to KS_AUTH_TRUE or KS_AUTH_FALSE Only KS_AUTH_TRUE is fully authenticated
Definition at line 152 of file ssl_common.h.
◆ multi_status
| enum multi_status |
Definition at line 578 of file ssl_common.h.
Function Documentation
◆ get_key_scan()
gets an item of key_state objects in the order they should be scanned by data channel modules.
Definition at line 732 of file ssl_common.h.
References ASSERT, tls_session::key, KS_LAME_DUCK, KS_PRIMARY, tls_multi::session, TM_ACTIVE, and TM_LAME_DUCK.
Referenced by handle_data_channel_packet(), print_key_id(), print_key_id_not_found_reason(), tls_authenticate_key(), tls_authentication_status(), tls_multi_process(), tls_rec_payload(), and tls_select_encryption_key().
◆ get_primary_key()
gets an item of key_state objects in the order they should be scanned by data channel modules.
Definition at line 755 of file ssl_common.h.
References tls_session::key, KS_PRIMARY, tls_multi::session, and TM_ACTIVE.
Referenced by cc_exit_notify_enabled(), check_send_auth_token(), multi_client_set_protocol_options(), receive_auth_pending(), receive_cr_response(), send_push_request(), tls_authentication_status(), tls_multi_process(), and tls_test_payload_len().